Ready for fishing? Oops, we meant Phishing. In our previous newsletter, we explored spear phishing, whale phishing and vishing. In today’s newsletter, we will explore three other types of phishing that most of us will likely encounter in our daily lives.
1. Smishing (SMS + Phishing)
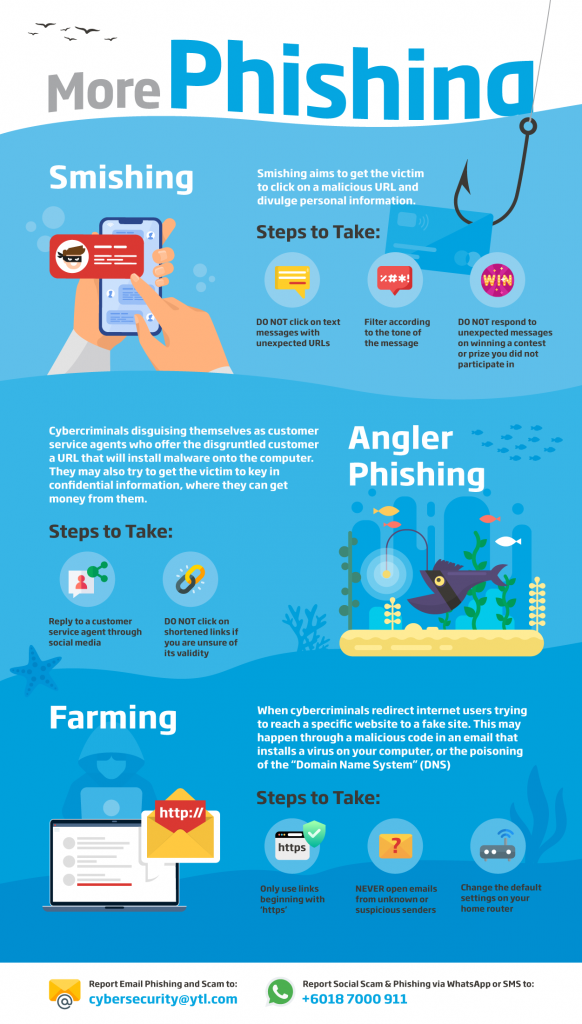
 What: Have you ever received a SMS from an unfamiliar number asking you to click on a URL? If so, then you have been a victim of Smishing. Smishing aims to get victim to click on a malicious URL and get the victim to divulge personal information.
What: Have you ever received a SMS from an unfamiliar number asking you to click on a URL? If so, then you have been a victim of Smishing. Smishing aims to get victim to click on a malicious URL and get the victim to divulge personal information.
How? By clicking on the URL, it might download a malware into your phone and the SMS malware could masquerade as a legitimate application tricking you to type confidential information. The cybercriminals receives your confidential information that allows them to steal your money and even hold you ransom.
How to detect & what to do?
- SMS containing a URL: If you receive a SMS with a URL and especially when you are not expecting it, do not click on it. If you receive a SMS with a URL you are expecting, but still doubtful, always verify with the organisation by giving them a call.
- Sense of urgency in the message: Approach urgent account updates and limited time offers as caution signs of possible smishing. Remain skeptical and proceed carefully.
- Unexpected message: A congratulatory message on winning a contest or prize that you did not participate. In such cases, do not respond as attackers depend on your curiosity to divulge sensitive information.
2. Angler Phishing
 What: With the rise of people posting their complaints about a product or service of a company on social media platforms, cybercriminals leverage on this opportunity by disguising themselves as customer service agents of the organisation through a fake account. The “agent” will offer the disgruntled customer a URL that will install a malware onto the computer or get them to key in their confidential information, where they can get money from them.
What: With the rise of people posting their complaints about a product or service of a company on social media platforms, cybercriminals leverage on this opportunity by disguising themselves as customer service agents of the organisation through a fake account. The “agent” will offer the disgruntled customer a URL that will install a malware onto the computer or get them to key in their confidential information, where they can get money from them.
How to detect & what to do?
- Reply from a customer service agent through social media: Always check to see if the social media account is verified & request for a follow-up through the company’s official email address instead over social media.
- Shortened URL: Cybercriminals will often use shortened links that look like a random string of letters. If you are unsure of the validity the link, do not click it. Instead take the customer service issues directly to the company’s website or call center for a resolution.
3. Pharming
 What: Pharming happens when cybercriminals redirect internet users trying to reach a specific website to a fake site. Through the fake site, cybercriminals will get victims to share their confidential information or may install malware on your computer. Pharming can occur when a hacker send a malicious code in an email that installs a virus or Trojan on your computer that redirects the traffic to fake website instead. Alternatively, the cybercriminal can poison the “Domain Name System (DNS)” and direct multiple users on the network to visit fake sites.
What: Pharming happens when cybercriminals redirect internet users trying to reach a specific website to a fake site. Through the fake site, cybercriminals will get victims to share their confidential information or may install malware on your computer. Pharming can occur when a hacker send a malicious code in an email that installs a virus or Trojan on your computer that redirects the traffic to fake website instead. Alternatively, the cybercriminal can poison the “Domain Name System (DNS)” and direct multiple users on the network to visit fake sites.
How to detect & what to do?
- Website links that being with HTTP: Use only links that begins HTTPS, where the “s” stands for secure which indicates the sites has a valid security certificate.
- Links and attachments from unknown senders: Never open emails from any unknown or suspicious senders. Most importantly, never open attachments or links in these emails.
- Is my home route in default settings? : If you have not changed your default settings of your home router, please do! Crate a strong password for your private network and never use the standard passwords. This will protect your local DNS from being poisoned.
 Report email phishing and scam to [email protected]. Report social scam & phishing via Whatsapp or SMS to +60187000911.
Report email phishing and scam to [email protected]. Report social scam & phishing via Whatsapp or SMS to +60187000911.
In summary, be smart, choose not to click URL and open attachments unless you are confident it is from a legitimate source. Also, you can prevent yourself from being a victim of angler phishing by being mindful of what you post on your social media accounts. Finally, make it a point to check that the website you are on begins with “https”.