by the Cybersecurity Task Force
Welcome to the next issue of our cybersecurity awareness initiative. Unfortunately, cybercriminals never sleep: you might have heard of the recent OCBC incidents in Singapore that caused nearly 790 customers to lose about SGD$13.7 million. How did they do it? By stealing login information, i.e. IDs and passwords. This is called “credential phishing”.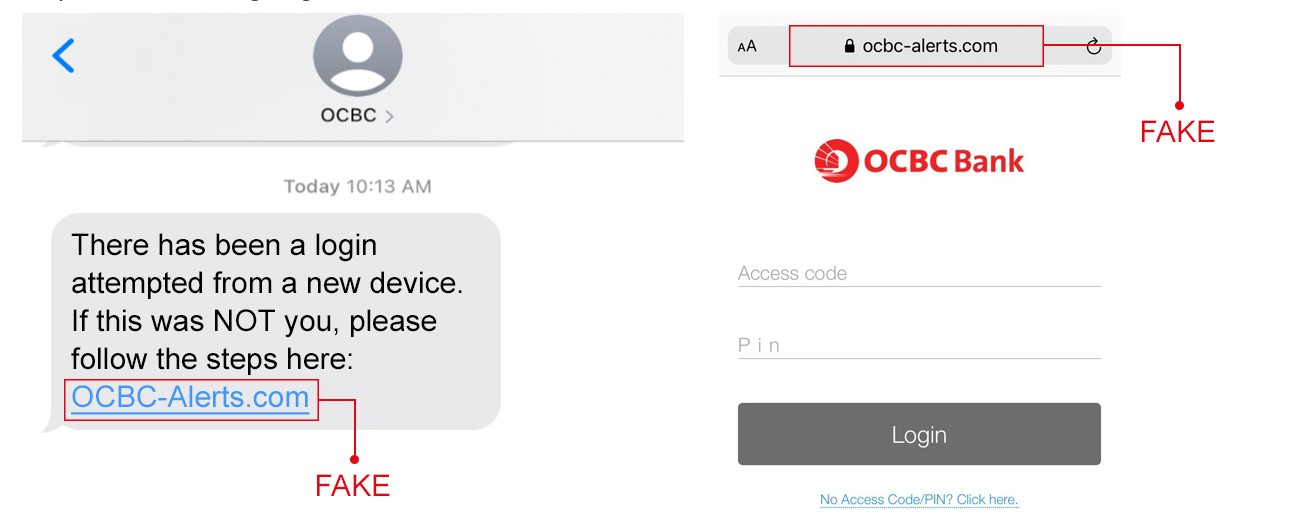 So today we, your trusty Cybersecurity Task Force, are pulling out a case file to walk you through what a credential phishing scenario looks like, then what you can do to guard yourself against becoming a victim. Ready? Let the cybercriminal hunting begin!
So today we, your trusty Cybersecurity Task Force, are pulling out a case file to walk you through what a credential phishing scenario looks like, then what you can do to guard yourself against becoming a victim. Ready? Let the cybercriminal hunting begin!
The Case File ?
It’s Monday morning. You sign in to your email and see a Document Review Request from an associated person, like a vendor or partner. In this example, we’ll call them ABC Vendor Bhd.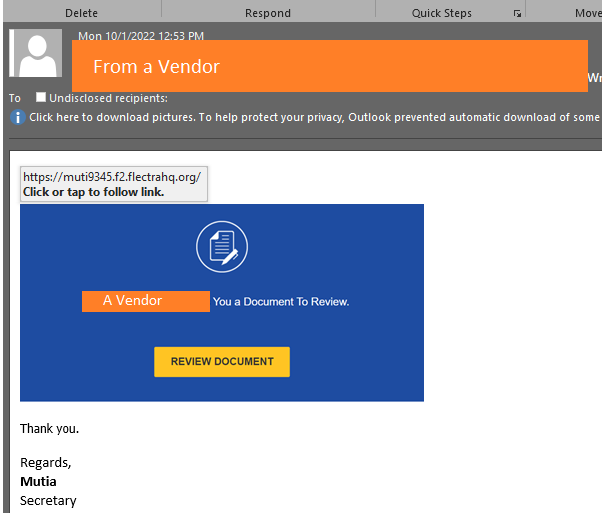 You were expecting them to contact you and nothing about the email looks fishy. So you click the link and are redirected to this page:
You were expecting them to contact you and nothing about the email looks fishy. So you click the link and are redirected to this page: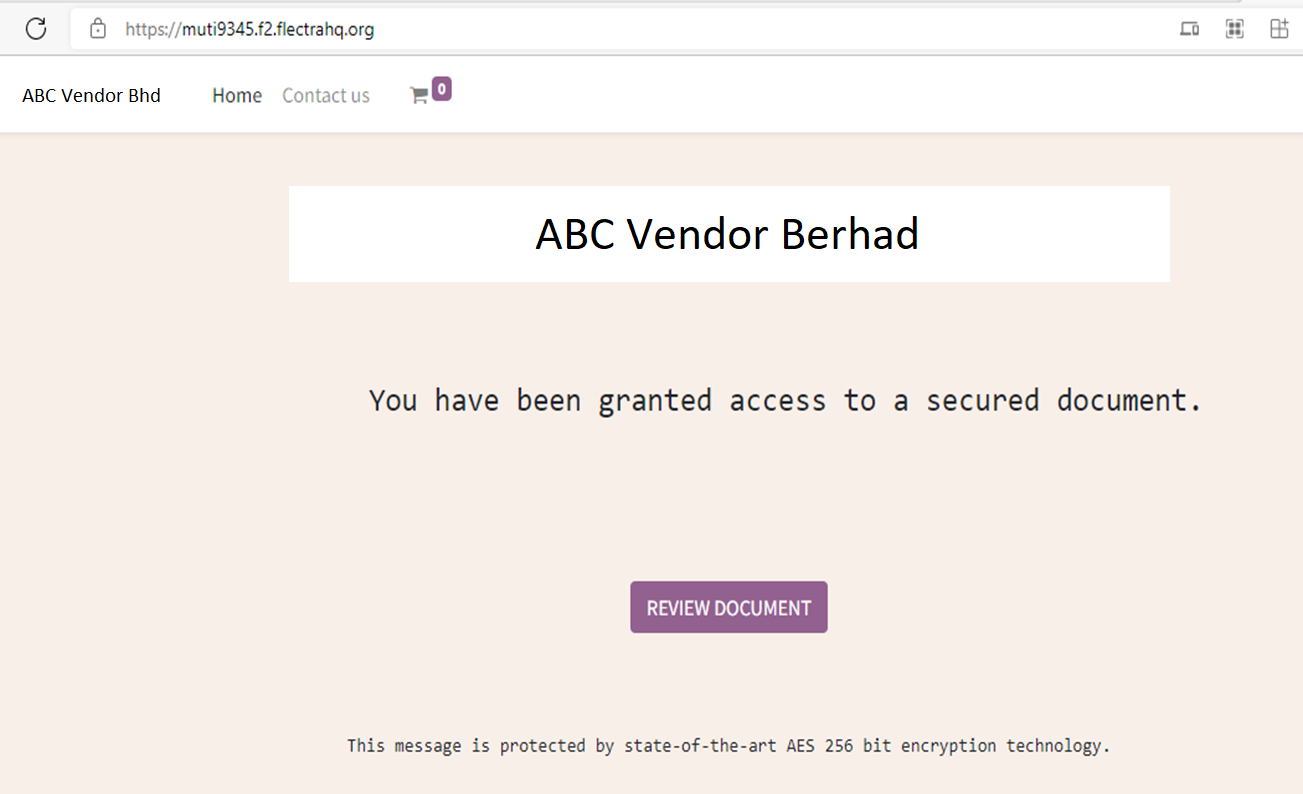 Hmm, it’s a vendor authorisation form containing another link to open the document. Looks legitimate too, so you click the button.
Hmm, it’s a vendor authorisation form containing another link to open the document. Looks legitimate too, so you click the button.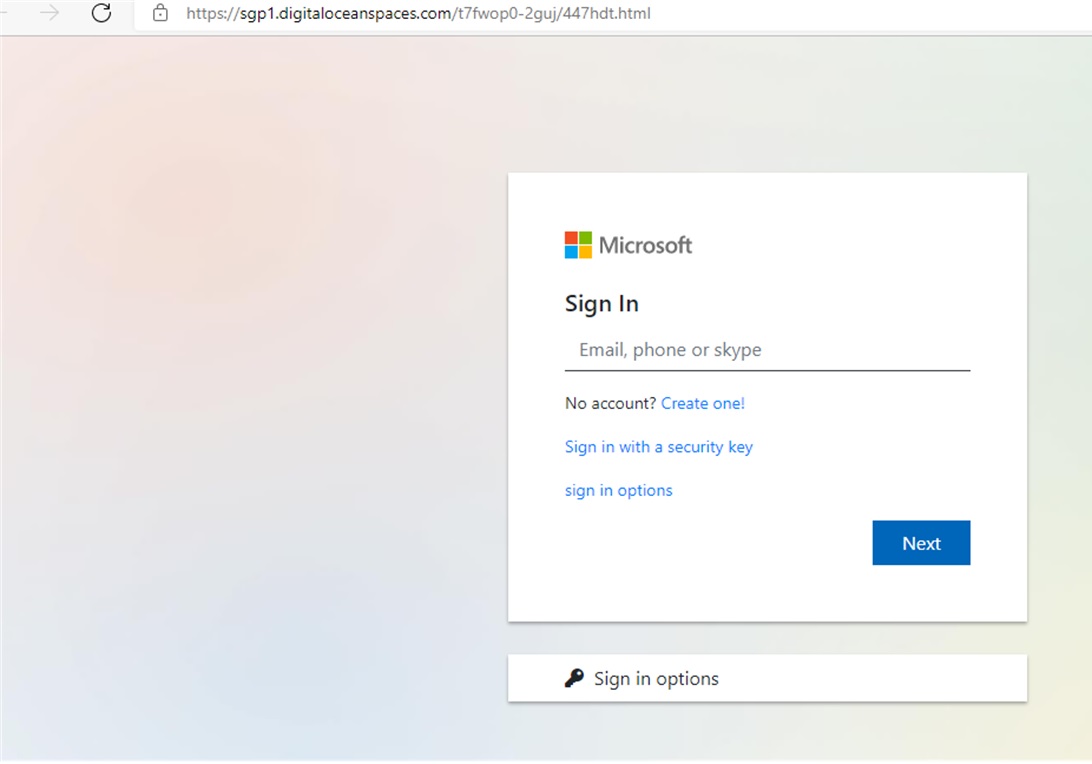 Ah, familiarity: a Microsoft login page. You key in your credentials and the next thing you know, someone has stolen your ID and password. How did this happen?
Ah, familiarity: a Microsoft login page. You key in your credentials and the next thing you know, someone has stolen your ID and password. How did this happen?
Investigation Time ?️
Ok, let’s take a step back and look at how could you have avoided becoming a victim of this kind of phishing. Here are some guidelines to remember:
- Do NOT click any links from any person or source you do not know.
- Even if the sender is someone you know, do NOT click the link from any unexpected email, SMS or WhatsApp message.
- Only log in directly from secure, trusted URLs. Do not key in your ID, password or OTP in suspicious links.
- Check the legitimacy of the URL domain name using the Google search engine.
In our case file, you know the vendor (1.) and were expecting an email from them (2.). But, the Microsoft login page URL and domain name (3. and 4.) should have raised a red flag. Today, we will teach you how to read and identify fake URLs and domain names. Learn well! Because next week (28 February), we will quiz you to test your skills.
How to Read URLs and Domain Names ?
Let’s start simple with what is a URL. A Universal Resource Locator (URL) (a.k.a. link) is the full address that your browser uses to find the website you want to visit. URLs comprise of three parts: a subdomain, top-level and second-level domain (a.k.a. the domain name) and the directory (a.k.a. parameters).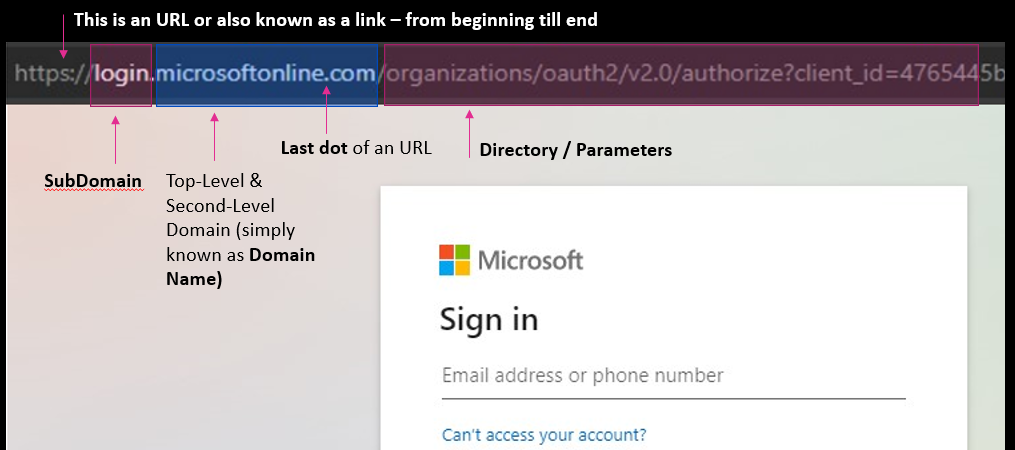 Generally, the domain name are the letters that sandwich the left and right of the last dot in the URL (see blue highlight in the image above). This rule applies to links ending with, for example, “.com”, “.net”, and “.org”. But for URLs with a country code like “.com.my” or “.co.uk”, you have to look at the letters surrounding the last TWO dots in the URL.
Generally, the domain name are the letters that sandwich the left and right of the last dot in the URL (see blue highlight in the image above). This rule applies to links ending with, for example, “.com”, “.net”, and “.org”. But for URLs with a country code like “.com.my” or “.co.uk”, you have to look at the letters surrounding the last TWO dots in the URL.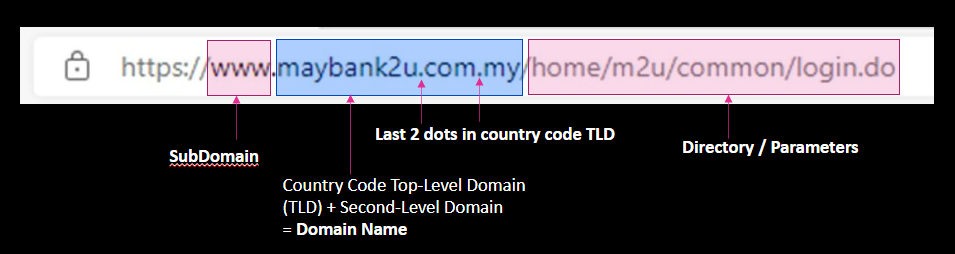 Just like the number on your identity card identifies only you, a domain name is a unique identity that is tagged to only a single organisation. Below is a comparison of the fake Microsoft login page from our case file, and Microsoft’s real page.
Just like the number on your identity card identifies only you, a domain name is a unique identity that is tagged to only a single organisation. Below is a comparison of the fake Microsoft login page from our case file, and Microsoft’s real page.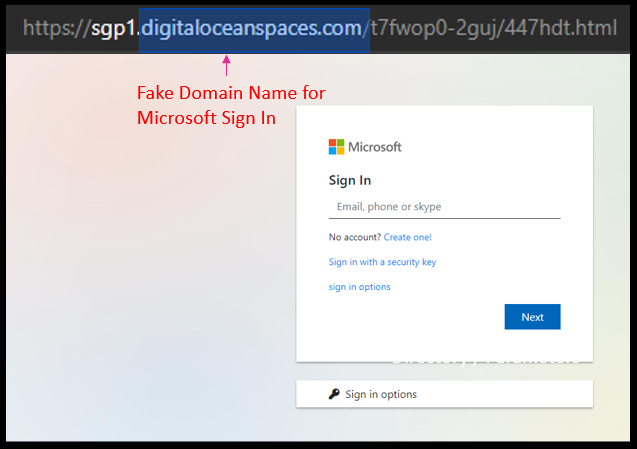
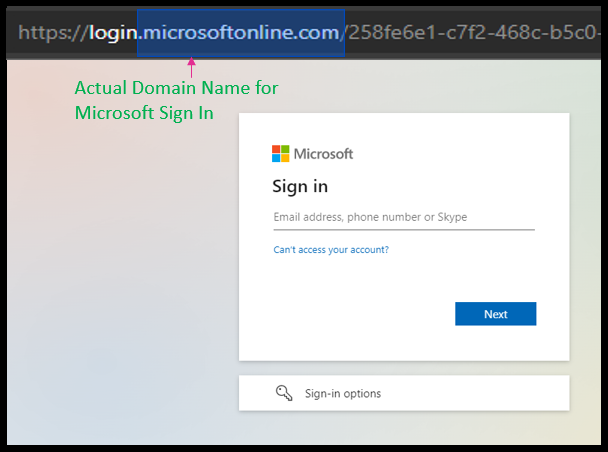 The key is to find the last dot in the URL. Let’s revisit the OCBC incident from the introductory paragraph. Their real domain name is ocbc.com. The following URLS are real because the domain name is still ocbc.com:
The key is to find the last dot in the URL. Let’s revisit the OCBC incident from the introductory paragraph. Their real domain name is ocbc.com. The following URLS are real because the domain name is still ocbc.com:
- https://Ocbc.com/transfer/etc/etc
- https://Me.ocbc.com
- https://etc.ocbc.com
But the following are all fake, so you should NOT login in via these URLs:
- https://ocbc-me.com – the domain here is “ocbc-me.com”
- https://ocbc.bank.com – the domain here is “bank.com”
- https://ocbc.etc.com – the domain here is “etc.com”
We hope that you feel more confident at reading domain names from URLs. It might take some time, but with some practice, you can do it! If you are still unsure whether or not the domain name is genuine, use the Google search engine or contact us at [email protected] or +6018 7000 911.